Fully Managed Security for firms that can’t afford to take chances.
We deliver 24×7, fully managed protection on all your identities, devices, and data – for the whole organization including personal devices – anywhere in the world. Using cutting edge tools and practices, we provide continuous human alert monitoring, security hardening, incident response, and remediation that is always a step ahead of the bad guys.

Today is a time of unprecedented external threat.
Identity security.
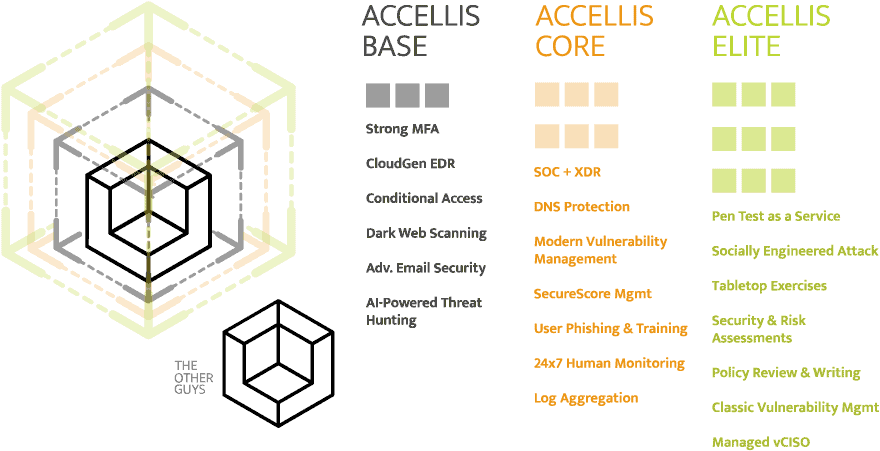
The first tenant of modern cybersecurity is protecting your end-users. Our Managed Security offering protects users with Multi-Factor Authentication (MFA), Conditional Access (CA), Single Sign On (SSO), DNS Protection, Dark Web Credential Monitoring, End-User Phishing & Training, AI-based Email Security (i.e., anti-spam, anti-spear phishing, anti-impersonation, anti-spoofing, domain fraud prevention, etc.) and much more.
Most breaches happen because a user makes a mistake; by using the right systems, automation, and AI, we can prevent the user from being tested in the first place.


Device security.
The second tenant of modern cybersecurity is protecting your devices (think servers, laptops, firewalls, etc.). Our Managed Security offering protects devices with incredibly advanced, yet cost effective, Endpoint Detection & Response (EDR), Security Operations Center (SOC), Extended Detection & Response (XDR), Vulnerability Management (Classic & Modern), Unified Endpoint Management (UEM), and more. And this protection covers not just the company’s assets but the employee’s personal devices (BYOD).
Okay, that’s a lot of acronyms. Making things much simpler: 24×7, elite security on all assets no matter where in the world those assets are.
Data security.
The third tenant of modern cybersecurity is protecting your data (think applications, databases, files, etc.). Our Managed Security offering protects your data with industry leading tools and practices such as policy development, penetration testing, tabletop exercises, custom training, hard disk and email encryption, Mobile Application Management, Data Loss Prevention, and much more.
Simply put, we don’t just make it hard to attack your end-users and to get into your devices; if they do get through, we make it even harder to extract your organization’s valuable intellectual property, customer records, PII, and more.

Key Deliverables of Managed Security
We’re in this with you.
We deliver 24×7, fully managed protection on all your identities, devices, and data – for the whole organization including personal devices – anywhere in the world. Using cutting edge tools and practices, we provide continuous human alert monitoring, security hardening, incident response, and remediation that is always a step ahead of the bad guys.
Stop double-spending on security.
Most organizations already own most of the tooling needed to execute this advanced security program on their existing Microsoft 365 license, only they don’t know they have these tools and they haven’t deployed them. Worse, many organizations also sign with a security vendor that sells them the same tools again, just from different vendors (i.e., Sophos, BitDefender, Symantec, DUO, Cisco Umbrella, AirWatch, etc.).
In short, they pay thousands of dollars per month for inferior copies of what they already own. Hard to believe? Give us a call and we’ll show you.

Be in the driver seat, not the trunk.
By utilizing Accellis’ Managed Security offering, which is powered almost entirely with tools you already own in your Microsoft 365 tenant, you are the boss not the lackey. If you’re unhappy with our service, there is no expensive conversion of tools and data from us to another provider. You own these tools, not us, so you don’t have to ask us for the keys… they are your keys, just hand them to a different Microsoft Gold partner.
Supportable, sweeping, and sustainable.
Supportable means the program is comprehensible not just to Accellis but to your internal IT team, too (if you have one). It means fewer panes of glass, subscriptions, vendors, and APIs, which lowers costs and risk. It means if you want to hire internally, you can look at internationally recognized standards and competencies such as MS-100, MS-500, etc. to know who can work with it.
Sweeping means it covers all users, devices, data, systems, applications, and behaviors spanning on-premises, remote-only, and hybrid workers, regardless where or when people work, and regardless of the device OS or who owns it. As new assets are added to your environment, coverage is automatically extended without the need for you or IT to do something.
Sustainable means it makes use of your existing investments in IT and personnel, it eliminates redundant vendors, solutions, hardware, and subscriptions, and net-new spending is purpose-driven and judiciously added. It means you have a predictable and scalable security program that you can understand on a per-user, per-site, per-business unit cost center basis.
Zero-trust security on all your IT, 24×7, 100% of the time. Get started, today.