Elite Cybersecurity Services Cleveland Businesses Need
We deliver 24×7 cybersecurity services Cleveland organizations can depend on. With our complete suite of network security solutions, you’ll enjoy protection on all your identities, devices, and data across the whole organization. This even includes personal devices – anywhere in the world. Using cutting edge tools and practices, we offer continuous human alert monitoring, security hardening, incident response, and remediation that is always a step ahead of the bad guys.

Full-spectrum network security in a time of unprecedented external threats.
Our managed cybersecurity services offer businesses an array of benefits that are vital in the contemporary digital landscape, marked by ever-evolving cyber threats. One of the primary advantages is the expertise brought to bear on an organization’s cyber defense strategy. Get access to a team of specialized security professionals who possess the knowledge and skills to address a wide range of threats and vulnerabilities.
Identity security.
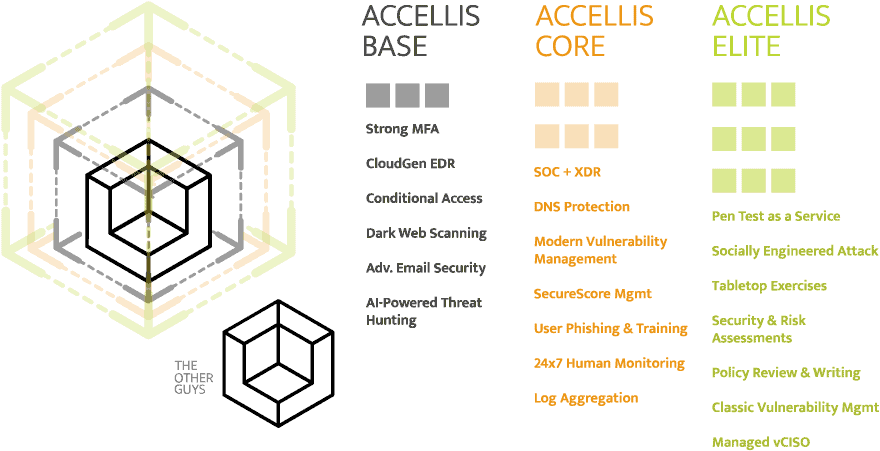
The first tenant of modern cybersecurity services is protecting your end-users. Our Managed Security offering protects users with Multi-Factor Authentication (MFA), Conditional Access (CA), Single Sign On (SSO), DNS Protection, Dark Web Credential Monitoring, End-User Phishing & Training, AI-based Email Security (i.e., anti-spam, anti-spear phishing, anti-impersonation, anti-spoofing, domain fraud prevention, etc.) and much more.
Most breaches happen because a user makes a mistake; by using the right systems, automation, and AI, we can prevent the user from being tested in the first place.


Device security.
The second tenant of modern network security is protecting your devices (think servers, laptops, firewalls, etc.). Our Managed Security offering protects devices with incredibly advanced, yet cost-effective, Endpoint Detection & Response (EDR), Security Operations Center (SOC), Extended Detection & Response (XDR), Vulnerability Management (Classic & Modern), Unified Endpoint Management (UEM), and more. And this protection covers not just the company’s assets but the employee’s personal devices (BYOD).
Okay, that’s a lot of acronyms. Making things much simpler: 24×7, elite security on all assets, no matter where in the world those assets are.
Data security.
The third tenant of modern cybersecurity services is protecting your data (think applications, databases, files, etc.). We protect your data with industry leading tools and practices such as policy development, penetration testing, tabletop exercises, custom training, hard disk and email encryption, Mobile Application Management, Data Loss Prevention, and much more.
Simply put, we don’t just make it hard to attack your end-users and to get into your devices; if they do get through, we make it even harder to extract your organization’s valuable intellectual property, customer records, PII, and more.